JBS Foods just admitted to paying an $11 million ransom to a ransomware group, after most of its meatpacking operations had already recovered from the attack.
Why?
The company said all along that its backups worked. And it shared multiple updates with statements like this one:
"The company is not aware of any evidence at this time that any customer, supplier or employee data has been compromised."
Why did JBS pay a ransom to cybercrime group?
So why pay a ransom? If we take the latest JBS statement at face value, the reason was to be proactive. Does this make sense?
Here is the company's June 10, 2021, statement. Give it a read and let us know what you think.
"JBS USA today confirmed it paid the equivalent of $11 million in ransom in response to the criminal hack against its operations. At the time of payment, the vast majority of the company's facilities were operational. In consultation with internal IT professionals and third-party cybersecurity experts, the company made the decision to mitigate any unforeseen issues related to the attack and ensure no data was exfiltrated.
'This was a very difficult decision to make for our company and for me personally,' said Andre Nogueira, CEO, JBS USA. 'However, we felt this decision had to be made to prevent any potential risk for our customers.'
The FBI stated this is one of the most specialized and sophisticated cybercriminal groups in the world. JBS USA's ability to quickly resolve the issues resulting from the attack was due to its cybersecurity protocols, redundant systems and encrypted backup servers. The company spends more than $200 million annually on IT and employs more than 850 IT professionals globally.
JBS USA has maintained constant communications with government officials throughout the incident. Third-party forensic investigations are still ongoing, and no final determinations have been made. Preliminary investigation results confirm that no company, customer, or employee data was compromised."
Twitter reacts to JBS ransomware payment
If we're following the narrative here, JBS did not lose any data, and it was able to restore the system from backups.
But the company paid a ransom anyway, just to be safe.
Those in the Twitter-verse had questions about this:
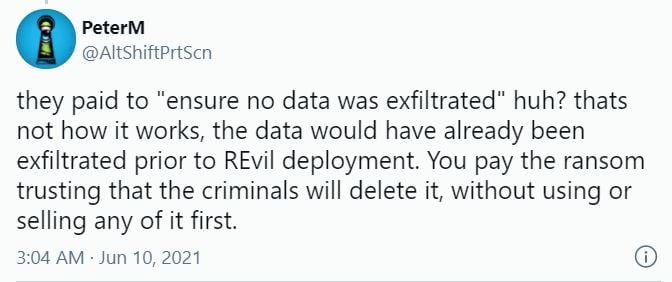
And that's why the company's public explanation of a ransom payment doesn't make sense.
[RELATED: Fallout and Blame: Ransomware Attack on World's Largest Meat Producer]
But an explanation published by Bleeping Computer may shed some light on this. The publication claims it has viewed the negotiations between the REvil cybercrime group and JBS, and that the original ransom demand was twice what JBS paid:
"We want to inform that your company local network have been hacked and encrypted. We have all your local network data. The Price to unlock is $22,500,000," REvil told the JBS representative.
And the publication says the company actually did need some help with decryption:
"JBS explained that they only needed the ransomware decryptor to decrypt two specific databases as the rest of the data was being restored from backups."
The hacking group also apparently threatened to publish exfiltrated data but claimed the file transfer would take place later on.
That part of the story certainly fits with the idea of proactively paying hackers who make a claim against you. Although this is a frightening precedent.
Remember this part of the JBS statement?
"...the company made the decision to mitigate any unforeseen issues related to the attack and ensure no data was exfiltrated."
This renewed calls for something to change. And there are a lot of possibilities for what that could or should look like:
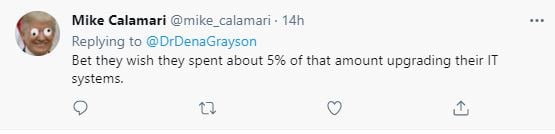
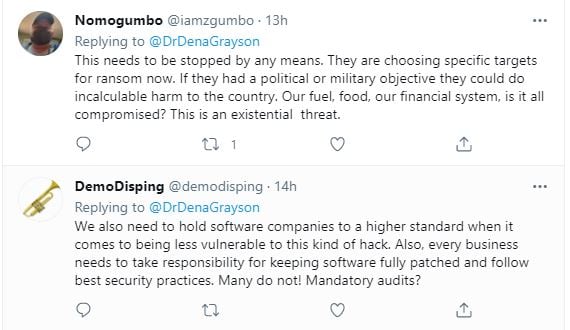
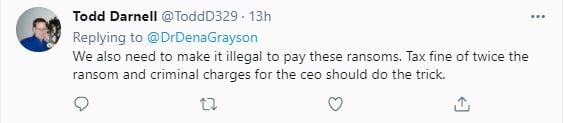
Should ransomware payments be made illegal?
This raises a great question: should ransomware payments be banned? Or are they an organization's best "frenemy"? After the Colonial Pipeline ransomware attack that left drivers searching for gas, the company CEO said paying the ransom was the best thing for the country.
This topic was the focus of our recent SecureWorld livestream interview with SpencerFane cyber attorney Shawn Tuma:
As it turns out, the answer to this question is complicated—just like a ransomware attack itself.



