Kevin Mitnick is KnowBe4's Chief Hacking Officer. And when he posted a brief YouTube video showing him hacking his way through multi-factor authentication (MFA), the marketing and PR department got blown up with questions, phone calls, and interview requests.
That was an eye-opening moment for Roger Grimes, who calls himself KnowBe4's data-driven defense evangelist.
"At that time, most of my friends in information security even thought MFA was hard to hack," Grimes says. "I can hack any MFA solution at least five or six different ways. And right now I'm writing my latest book on the topic, and it looks like I'll be able to document close to 50 ways to defeat MFA."
Defining multi-factor authentication (MFA)
Grimes led the SecureWorld web conference 12 Ways to Defeat Multi-Factor Authentication, and How to Stop the Bad Guys, which is available on-demand.
As you likely are aware, MFA is a digital authentication solution based on various attributes.
These could be through things you know (like a password or PIN), things you have (like a USB token), something you are (biometrics), or other factors (like device location confirmation). Says Grimes:
"If you want MFA to be strong, you have to require different categories of factors. Like a PIN and a smartcard, for example. It's hard for an attacker to phish your PIN and get your physical smartcard at the same time. That increases your security."
MFA attacks, approaches that work
At the highest level, Grimes says hackers use several approaches. Social engineering is crucial, there are technical attacks against underlying technology, and physical attacks like biometric theft, for example.
And some of the attacks involve two or more methods and are helped by insecure transitioning between linked steps, such as identity, authentication, and authorization.
Defeating multi-factor authentication in a Network Session Hijack
Grimes started by looking at what he calls a "super easy" attack, which Kevin Mitnick demonstrated after Grimes described it.
The MFA attack is known as Network Session Hijacking, and Grimes says millions of accounts have been compromised in this type of attack.
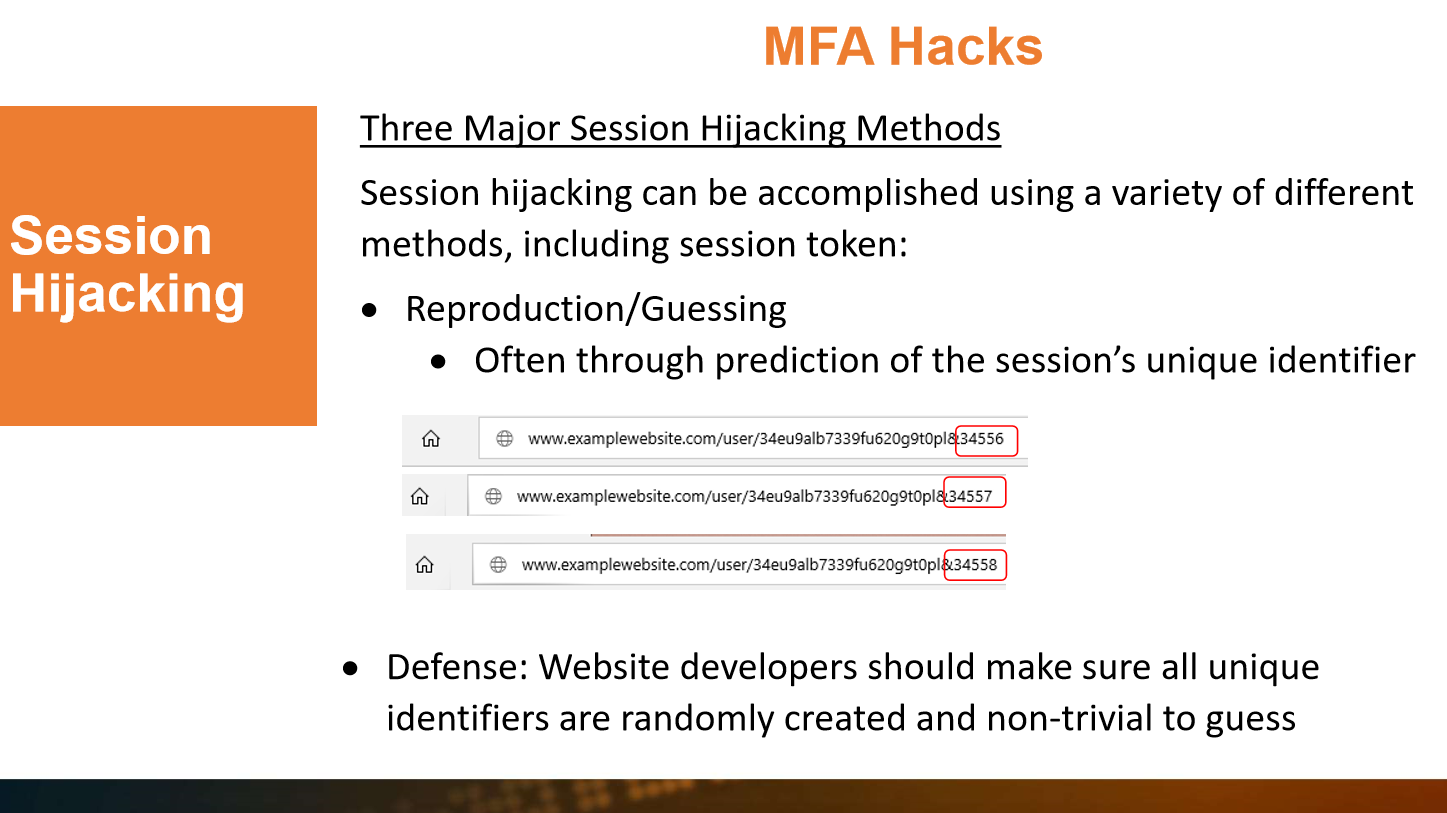
Says Grimes:
"It is probably the most common type of hacking to get around multi- factor authentication. It usually requires a man-in-the-middle attack. So there has to be an attack for this somehow. In between the client and the server, the attacker puts them inside of this legitimate communications strain. And then the attacker waits for the regular user to authenticate. And then they spill the legitimate resulting access control token.
So usually what the attacker will do, is a man-in-the-middle session, and then they'll put an evil proxy website in the middle of that, that neither the client or the server knows about.
And they will proxy the website to the user and everything the user types or clicks on the website, and then spill all the information between the two waiting for that authentication to be successful.
They don't care whether you authenticate your login name and password or multi-factor or a 10-factor solution. They're just waiting for that access control token to get compromised."
During the web conference, Kevin Mitnick then performed this type of attack, and sure enough, it was easy and only took a couple of minutes.
Other types of MFA attacks detailed
Grimes then continued his presentation, covering more than a dozen types of MFA attacks that work, including real-world examples of where attackers have used them.
- Man-in-the-endpoint attacks
- SIM swapping attacks
- SMS-based MFA attacks
- Duplicate Code Generator Attacks
- Account/password recovery attacks
- Hijacking Shared Auth & APIs
This is just a partial list; there are many more in the web conference.
Protecting against MFA attacks
If attacks on MFA are easy and there are so many of them, does MFA make sense? Roger Grimes still believes it does.
"I don't want to say multi-factor is terrible. All things considered, it is generally better than single-factor and we should strive to use it wherever it makes sense and is possible. However, if someone tells you something is unhackable, they're either lying to you or dumb."
We've heard similar sentiments discussed at SecureWorld conferences. There are no no silver bullets in security. We know this.
In the case of MFA, Grimes says top defense techniques include education for both admins and end-users. This should include MFA hacking awareness as part of your security awareness training.
He listed more defense specifics in the web conference.
12 Ways to Defeat Multi-Factor Authentication, and How to Stop the Bad Guys is available on-demand.
We think you'll find this cybersecurity web conference to be extremely informative and helpful in the effort to protect your organization.




