Zero Trust Architecture (ZTA) is gaining significant traction among organizations as a new security framework. This strategic cybersecurity model challenges the traditional assumption of trust within networks, aiming to bolster data protection and minimize the risk of cyberattacks.
A Cybersecurity Insiders survey revealed that as of 2021, 72% of organizations have either implemented or are in the process of adopting Zero Trust Architecture. Furthermore, Gartner predicted that by 2023, approximately 60% of enterprises will have embraced this framework, compared to less than 10% in 2020.
Forrester conducted a study showing that organizations adopting ZTA experienced 30% fewer security incidents and 40% less severe security breaches than those relying on traditional security models. Additionally, the 2021 Zero Trust Progress Report by Pulse Secure found that organizations that embraced ZTA reported a remarkable 63% reduction in data breaches compared to the previous year.
One of the fundamental advantages of Zero Trust Architecture lies in its ability to enhance data protection. Segmenting sensitive data into smaller, more manageable units significantly reduces the risk of unauthorized access or lateral movement within a network. A report by Cybereason highlighted that 81% of organizations implementing ZTA reported improved data security and decreased data exfiltration incidents. ZTA enforces continuous authentication, authorization, and validation for all entities attempting to access resources. This approach ensures that users and devices prove their identity and validate access privileges throughout their session.
According to a survey conducted by Pulse Secure, 78% of organizations implementing ZTAwitnessed improved control over user access and permissions. Furthermore, ZTA plays a crucial role in enabling secure access to cloud resources and supporting remote workforce scenarios. ZTA ensures secure connections regardless of the network or location by verifying identities and validating devices. A study by Zscaler found that 96% of organizations believed ZTA was essential for securing cloud-based applications and remote work environments.
These statistics show that ZTA offers compelling benefits to organizations, including reduced security incidents, enhanced data protection, improved access control, and secure cloud and remote workforce enablement.
Here are some examples of Zero Trust Architecture:
- Google's implementation of ZTA, known as BeyondCorp, is an excellent example. BeyondCorp eliminated the concept of a trusted internal network, requiring all devices, regardless of location, to undergo strict verification before accessing Google's resources. As a result, Google observed a significant reduction in successful phishing attacks and increased overall security posture.
- Dropbox implemented a system called Project Infinite, which includes a rigorous authentication process, continuous monitoring of user activity, and robust encryption. This helps ensure that only authorized users have access to data and prevents unauthorized access attempts.
- Cisco's SecureX provides centralized visibility and control over networks, devices, and applications. It enforces strict access controls, including multi-factor authentication and micro-segmentation, to minimize the potential attack surface and protect critical resources.
- Microsoft Azure Active Directory (Azure AD) is a cloud-based identity and access management service that supports Zero Trust principles. Azure AD offers features such as conditional access policies, risk-based authentication, and privileged identity management, enabling organizations to implement Zero Trust security measures for their cloud-based resources.
Despite the growing popularity and recognition of ZTA as a robust security framework, many organizations need help implementing and realizing its full benefits. Recent data from industry research firms highlights organizations' struggles when adopting Zero Trust principles.
According to Gartner, a leading research and advisory company, it is projected that over 50% of organizations will fail to realize the benefits of Zero Trust by 2026. Additionally, Forrester reports that 63% of organizations need help implementing Zero Trust. These figures indicate that while Zero Trust is gaining traction, practical implementation remains a major obstacle for many.
Even with the Biden Administration's mandate for federal agencies to adopt Zero Trust, organizations across various sectors grapple with the complexities of deploying effective Zero Trust initiatives. Despite the changes in the threat landscape and the need for advanced security measures, organizations still need to overcome significant headwinds in their journey toward Zero Trust maturity.
[RELATED: White House Announces New National Cybersecurity Strategy]
One of the primary challenges lies in achieving a mature and measurable Zero Trust program. Gartner's research reveals that only 1% of organizations have successfully established such a program. This indicates a considerable gap between the theoretical benefits of Zero Trust and the practical implementation on the ground.
Several factors contribute to these challenges. First, implementing ZTA often requires significant changes to existing network infrastructure, applications, and security controls. The complexity and resource-intensive nature of the implementation process can impede progress and delay the realization of benefits.
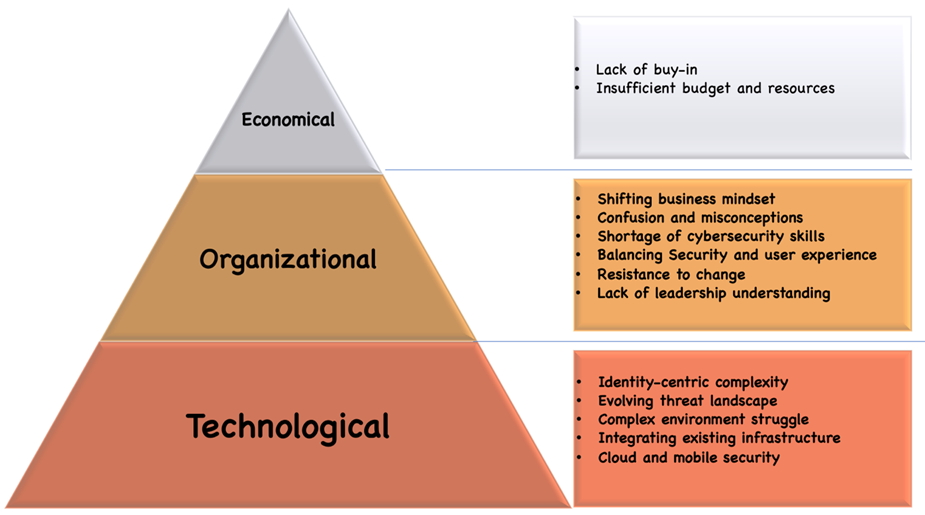 Zero Trust Implementation Challenges
Zero Trust Implementation Challenges
Additionally, the need for more skilled cybersecurity professionals poses a significant challenge. Organizations often need help finding and retaining personnel with the necessary expertise to design, implement, and manage a robust Zero Trust program. The lack of in-house capabilities can hinder progress and result in suboptimal deployments.
Furthermore, measuring Zero Trust initiatives' effectiveness and return on investment (ROI) remains challenging for many organizations. Demonstrating tangible outcomes and quantifying the impact of Zero Trust on security posture and risk reduction can take time, leading to difficulties in securing funding and executive support for ongoing implementation efforts.
Organizations must approach Zero Trust adoption with a well-defined strategy to address these challenges. This strategy should include thorough planning, assessing the current security landscape, setting realistic goals, and engaging in continuous monitoring and evaluation to ensure progress and identify areas of improvement.
Collaboration with trusted vendors and partners, who can provide guidance and expertise, is also essential. Leveraging external resources and expertise can help organizations navigate the complexities of Zero Trust implementation and optimize the deployment process.
As the Zero Trust landscape continues to evolve, organizations must learn from the experiences of early adopters, invest in adequate training and skill development, and remain adaptable to changing requirements and emerging technologies. With careful planning, perseverance, and the right resources, organizations can overcome the challenges associated with Zero Trust and successfully implement a mature and effective security framework.





