We've already reported on how tech companies were the focus of the CCleaner attack revealed last week.
Now comes a very interesting Monday update from Avast, the parent company of CCleaner. The math on this one is incredible.
"Worth noting is that about 40 PCs out of 2.27M had the compromised version of CCleaner product installed, i.e. 0.0018% of the total—a truly targeted attack."
CCleaner attack aimed at enterprise tech and telcos
In other words, more than two million PCs downloaded the infected version of CCleaner, but a secondary payload was sent to only 40 of those.
"That is, despite the fact that CCleaner is a consumer product, the purpose of the attack was not to attack consumers and their data; instead, the CCleaner customers were used to gain access to corporate networks of select large enterprises," Avast said in an updated blog post on September 25, 2017.
Domains infected with malicious codeThe post also details the list of domains where the second stage payload was successfully delivered.
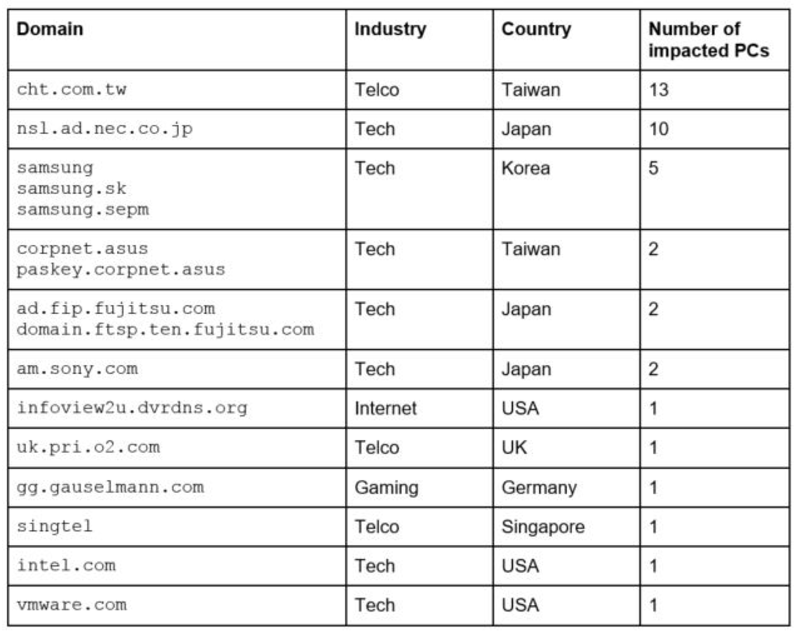
Analysis continues on bad actors behind CCleaner attack
Avast and Cisco Talos, among others, have suggested this looks a lot like a nation-state attack. There is evidence that points toward China. China is on the list of top three biggest cyber threats to the United States, as the former Director of Operations at U.S. Cyber Command told SecureWorld in this video interview.
Do you notice there are no Chinese tech companies on the target list? Also absent, however, are Russian and Indian companies. So at this point, the evidence remains inconclusive.
"... there were multiple clues suggesting that the attack may be originating from China, including multiple instances of PHP code found on the
There is more to come on this story. For the latest developments and original stories about cybersecurity, follow SecureWorld on LinkedIn, Twitter, or Facebook.




