We live in a world of stovepipes
Seven years ago, cyber incidents cost the world $500 billion. Four years ago, the price quadrupled to $2 trillion. By 2024, the total is expected to reach $4 trillion. To put this into perspective, every year we lose the equivalent of the combined GDP of Great Britain and France to cyberattacks.
What's causing this? Well, it's never a good idea to leave potential points of access unguarded in the face of known threats, is it? Yet we continue to create stovepipes. Operationally, cybersecurity ensures the electronic part of the operation, but it isn't interested in the human element. Naturally, there are parts of the organization accountable for ensuring people's good behavior, such as managers and human resources; but they don't want anything to do with the mysteries of cyberspace. While at the same time, physical security doesn't see any relationship between what they do and mysterious abstractions like electronic information assurance.
I hear you asking, "Who's going to knock down those stovepipes?" Well, the people presently running our organizations certainly aren't. Only 38 percent of the top executives surveyed by ISACA felt that they were accountable for doing anything substantive about cybersecurity. At the same time, not a single one of the sectors in the critical infrastructure has published a sector-wide strategy for top-down cybersecurity. There isn't even consistent agreement about what would constitute a critical breach. So, even with the clear evidence that very bad things are happening, you could reasonably characterize the current C-suite's response as "detached."
Every hazard must be addressed
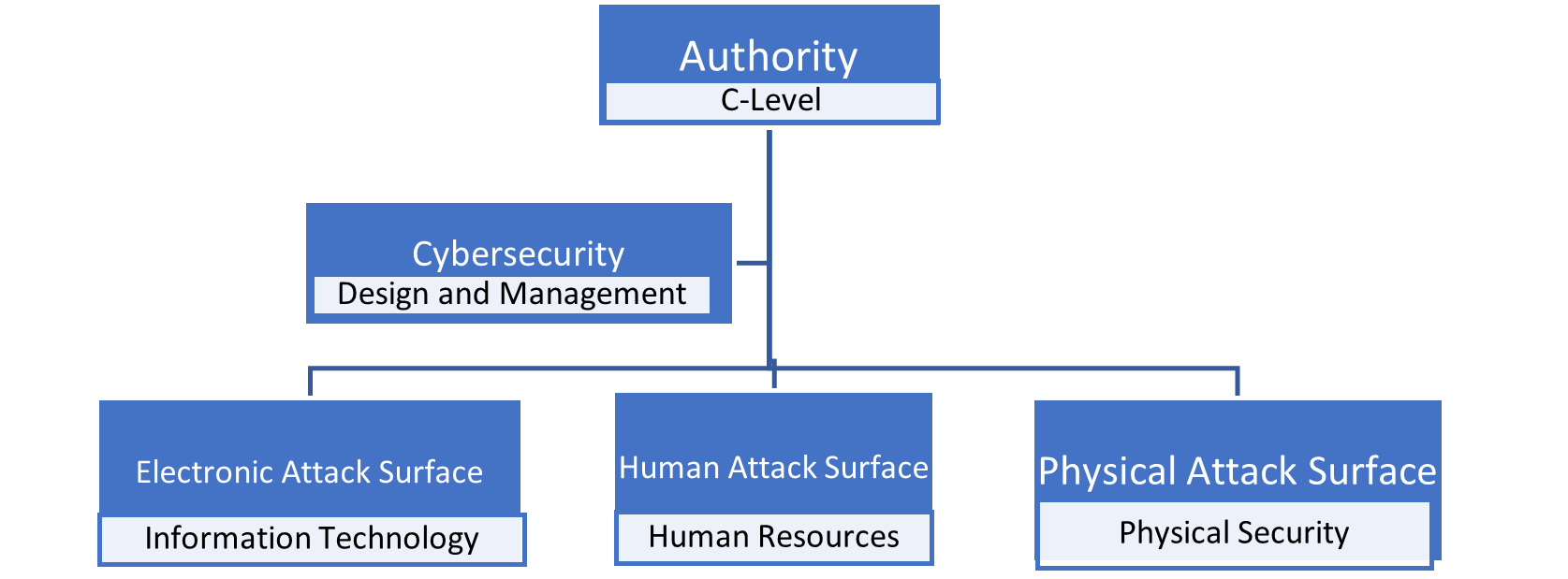
It should go without saying that an effective cyber defense needs to address every potential hazard. Nevertheless, the part of the organization responsible for what we normally term cybersecurity, e.g., Information Technology, only addresses a third of the problem. That is a dangerous approach because the past 25 years have taught us one indisputable fact: cyber exploits target THREE attack surfaces, not just one. Consequently, a proper defense will require unified command and control over all three points of access.
For ordinary people, the most obvious type of attack is purely electronic: hacking, malware, and all the other creative forms of digital penetration. But those attacks don't cause the majority of the problem. The rest of the damage, approximately 70 percent, is attributable to exploits such as social engineering and insider threat, along with real-world abuses, such as physical theft, break-ins, and simple loss due to accidents. A 10-year study by the Privacy Rights Clearinghouse supports this. It found that purely electronic exploits account for only around 29 percent of the total loss. While the actions of human beings, and physical incidents, account for the other 71 percent.
The adversary doesn't play by the rules
The adversary's goal is to break into your system by any means possible. So, the adversary will employ "anything that works." Hence, any hole in the protection scheme, be it electronic, behavioral, or physical, is a potential point of exploitation for the entire system. Or in simple terms, any electronic, human, or physical exposure that permits unauthorized access essentially negates the measures set up to secure the other two attack surfaces.
So, since the adversary will exploit any available point of entry, the organization's defensive perimeter needs to incorporate every control necessary to ensure comprehensive protection. Then those controls have to work together to safeguard the organization from all three potential forms of compromise. Thus, a well-defined and managed array of countermeasures is essential. That is the reason why a fully integrated set of interoperating behaviors is required for a complete solution.
Convergence is the key
The term used to describe the creation of a fully comprehensive and unified solution is "convergence." Convergence is a word that describes the merger of all relevant electronic, personnel, and physical security functions into a single strategic process. Convergence represents the unitary point of control that is always required to deploy and oversee a complex, rational, organization-wide cybersecurity protection scheme without exploitable gaps.
The steps necessary to achieve convergence are no less complex than the computer system design process. Mechanisms must be implemented to monitor the cybersecurity process across every potential point of access across the entire organization. These mechanisms must provide an integrated collection of mutually supporting controls, as well as make stakeholders accountable for their performance. A single coordination point is necessary because every organization's monitoring and enforcement requirements are cross-functional. So, that dedicated organizational entity has to have the authority to reach across the organization and enforce all of the elements of the cybersecurity scheme.
By its nature, comprehensive cybersecurity control deployment and sustainment must cross unit boundaries. That requires establishing a formally authorized strategic operation with the mandate to develop a fully integrated protection strategy and enforce it across every nuance of the organization's three attack surfaces. The organization must also identify and address all interdependencies. That is because control interdependencies are points of vulnerability that are often hard to identify because they involve multiple attack surfaces, which makes assurance a three-dimensional problem. In that respect, then, a converged approach will ensure optimum situational understanding.
As we said, Information Technology, which is the conventional unit responsible for cybersecurity, is too low in the hierarchy to do this effectively. Logically, individual execution of the control requirements must be consistent across all attack surfaces for the organization. Therefore, the key to achieving convergence is proper organizational placement. Only top-level managers have the authority and scope to initiate and enforce the implementation of a converged package of protection measures. So, the accountability inevitably falls to them, not to people down the organizational ladder.
Joint security operations centers enable convergence
That is the role of a Joint Security Operations Center (JSOC). Organizations typically foist the responsibility for cybersecurity onto the IT operation. That is because top-level decision makers think that all cybersecurity threats are electronic. Information Technology can do an excellent job of addressing computer and communication technology-oriented threats. But realistically, the people in IT don't have the interest or ability to define universal best practices for human and physical security. Even if they did, the organization's IT unit is powerless to enforce them across organizational lines.
A JSOC is the merger of existing security capabilities into a converged form. It does NOT require a massive investment in equipment and staff. But it DOES require a change in thinking within the organization since JSOCs require changes in organizational placement and authority. The aim is to locate the functional responsibility at a level sufficient to enable convergence to take place.
What does this mean for you?
Comprehensive and effective cybersecurity requires proper electronic, behavioral, and physical security expertise. JSOCs enable the design, deployment, and oversight of a complete organization-wide control solution that covers all documented dependencies. However, the location has to be at the strategic management level to ensure proper coordination and enforcement. That new location does not require a massive investment in resources since most of what is needed to do the job probably exist at the organization's lower levels. But it does require the vision to see and deal with the entire problem, not just the things that the organization wants to address.





