There’s been talk for years now that security needs to be baked into IoT (Internet of Things) device development.
While needed, that’s just a single dimension solution to a multi-dimensional cybersecurity challenge.
IoT expert Craig Spiezle did a level set on this reality in the SecureWorld web conference, “What’s Next on the IoT Threat Horizon?” The web conference is available on-demand and offers attendees CPE credits.
Spiezle, who has testified before Congress about the IoT, is Managing Director of AgeLight Advisory Group and Chairman Emeritus of the Online Trust Alliance.
IoT security is a three-dimensional problem
He says securing the IoT is a three-dimensional problem.
“One of the things that makes the IoT unique is that almost all of the devices are using the cloud. So data is going back and forth to the cloud. And many of these devices are in some way connected to an app. So perhaps you have a secure device and secure cloud,” but what happens, he asks, when the associated app is hacked and takes control of the device?
IoT security risk: the game has changed
Ron Winward, Security Evangelist at Radware, is always tracking the latest IoT security trends, and he told web conference attendees the risk to—and from—the IoT is at a whole new level.
“The last year, year and a half, has really changed the threat landscape for us.”
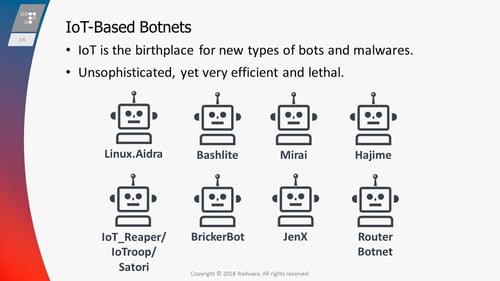
Factory default credentials have been a huge factor, he says, along with botnets created from disclosed vulnerabilities. He calls these IoT botnets the "ultimate weaponry."

He also showed specific examples of botnets responsible for spreading malware.
Market for IoT devices continues to grow
Against this backdrop of the growing IoT threatscape, Ravi Thatavarthy, Chief Information Security Officer at iRobot, detailed the explosive IoT opportunity devices. His company, alone, has sold more than 20 million robots.
He says we're headed for a time where each home will have hundreds of sensors.

“We are living in a world of connected products, however, there are certain things we must do to avoid disruption in this growth."
He cited four key things with regard to security:
- Secure identities
- Secure communications
- Secure storage
- Secure execution
He also talked about how crucial privacy will be in the IoT, and says his belief is security combined with privacy will become a brand differentiator.
IoT law trends in the United States
Attorney Tracy Lechner brought her legal expertise on the IoT ecosystem to the web conference. She is a shareholder and Head of the Cybersecurity, Privacy, Technology Transactions, Licensing and Advanced Media Practice at Brownstein, Hyatt, Farber, & Schreck.
She pointed out that the effort to more greatly secure the IoT has been underway for several years now and actually started with industry.
“Back in 2016 some major tech companies… offered a plan to help boost the security of IoT devices, they argued for a major shift in the way manufacturers approach IoT security. This included the idea that IoT devices default to allow no inbound traffic until the end user configures them.”
Now, she says, there are several attempts at legislation before Congress on the topic, including the IoT Cybersecurity Improvement Act, which was first introduced in 2017.

And she talked about areas that courts still need to address regarding IoT liability: If a device hurts you or leads to harm, which part of the three-dimensional security puzzle is liable? Would it be the device manufacturer, the cloud provider, or perhaps the app creator?
These questions will likely be answered in future litigation.
Ways to mitigate IoT risk
The SecureWorld web conference experts also talked about specific ways to mitigate risk from IoT, including some practical ideas InfoSec professionals can implement right now.
If you need to get up to speed, fast, on IoT security, register for “What’s Next on the IoT Threat Horizon?” and watch on-demand.
Afterward, you’ll be able to speak with authority on IoT security trends, and you’ll have some fresh CPEs and actionable takeaways, as well.




