Ali Alzabarah, a 35-year-old citizen of Saudi Arabia, earned computer science degrees in the U.S. and lived in the Bay Area while working as a reliability engineer at Twitter.
Twitter insider threat case: the reliability engineer
Alzabarah wrote to a Saudi government official that his greatest achievement was not his career, it was being an insider threat—a rogue Twitter employee—on behalf of the Saudi government.
"Today I became officially a member of the technical team at Twitter, this is the fifth tier out of six for engineers in companies in the Silicon Valley... My happiness is unimaginable and wanted to share with you the good news... thank you for supporting me and everything... As much as I am happy for the position, I am happier with and very proud of my work with you."
The FBI found that note during a search of his Apple account. And it was one piece of a larger scheme which revealed his work for leaders in Saudi Arabia.
Says the U.S. Department of Justice:
"Specifically, representatives of the Kingdom of Saudi Arabia and the Saudi Royal Family sought the private information of Twitter users who had been critical of the regime."
Who would have more access to Twitter users than a Twitter employee?
Twitter insider threat case: the partnership manager
41-year-old Ahmad Abouammo was a media partnerships manager for Twitter, responsible for the Middle East North Africa (MENA) region.
The FBI describes his role at the company:
"...was involved in assisting notable accounts of public interest, brands, journalists, and celebrities for the MENA region with content, Twitter strategy and sharing best practices."
And the FBI says Abouammo:
"Had access to proprietary and confidential Twitter information, including information about Twitter users, including the user-provided email addresses, birthdates, phone number and IP addresses."
This information and the story about Twitter's insider threat case is based on an indictment of three men in U.S. District Court. Two of those men were Twitter employees.
And each of them are charged with acting as illegal agents of a foreign government.
Assistant Attorney General for National Security, John Demers, sums up the case like this:
"Acting in the United States under the direction and control of Saudi officials, the defendants are alleged to have obtained private, identifying information about users of Twitter who were critical of the Saudi government."
Twitter insiders: how the crime started
The DOJ says in Abouammo's case (he was the media partnerships manager), it started with a watch given to him at a meeting with a Saudi official.
This was not a Timex. It was a used Hublot Unico Big Bang King Gold Ceramic Watch purchased for $20,000. Gold, sapphire, and titanium do not come cheap.
And they were certainly enough for Abouammo to fall in line.
Within a week of that meeting where he received the watch, the indictment says he began accessing private Twitter user information of interest to a Saudi official "and the Saudi Royal Family."
"Based on the FBI's review... [the target] was a prominent critic of the Kingdom of Saudi Arabia and the Royal Family with over 1,000,000 Twitter followers."
He is accused of researching and revealing details on a number of Twitter targets.
As his insider work for the Saudis continued, he allegedly registered as a Limited Liability Corporation (LLC) and used that company to receive $100,000 from the Saudi official.
Later, another $100,000 went from that official to one of Abouammo's relatives in Beirut. In all, he and his family received $300,000.
Abouammo responded with loyalty. He promised in a Twitter direct message to that official: "Proactively and reactively we will delete evil my brother."
Back to the Twitter engineer
Now, back to Alzabarah, the Twitter engineer who wrote about being proud of his work for the Saudis.
It turns out, he was using his Twitter-owned laptop to help his homeland. Now, there's something to send a shiver up the spine of cybersecurity professionals.
In Apple iMessages found on the laptop, he had messaged his wife about leaving for a sudden meeting with a Saudi official in Washington D.C.:

Alzabarah, a citizen of Saudi Arabia, seemed to be helping his country out of loyalty more than anything else.
The U.S. indictment reveals the depth of his work:
"...accessed without authorization through Twitter's computer systems the Twitter user data of over 6,000 Twitter users, including at least 33 usernames for which Saudi Arabian law enforcement had submitted emergency disclosure requests to Twitter."
Take a look at the kind of information he was sharing—information a government could use to track its critics like prey:
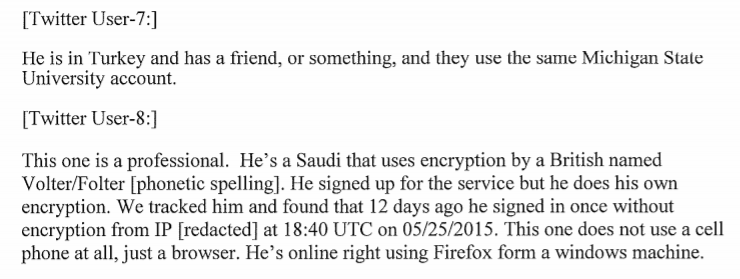
Another target he tracked, the FBI found, was:
"...a well known critic of the government and Royal Family of Saudi Arabia with asylum in Canada."
How the Twitter insider threat case ended
The newly unsealed court documents reveal this case took years to build. And it also pulls back the covers on how the investigation ended.
On December 2, 2015, Twitter confronted Alzabarah, placed him on leave, seized his company-owned laptop, and escorted him from the building.
The FBI says he then contacted the Saudi official he'd been working with, called the Saudi Arabian Consul General, and the next morning boarded a flight to Saudi Arabia with his family.
While on that flight, he sent a resignation notice to Twitter. And guess who hired him back home? The indictment says:
"Shortly after his return to Saudi Arabia, Alzabarah obtained employment through which he continued to work on behalf of the Kingdom."
He's never returned to the United States.
As far as Abouammo, the media partnerships manager at Twitter, he was confronted by the FBI in October of 2018.
When asked about the watch and the money, he told the FBI the watch he'd received was only worth $500 and that he'd been paid $100,000 for legitimate consulting work. Never mind the fact the FBI had already traced $300,000 flowing to him or his family.
Abouammo is the only one of the three suspects still in the U.S. He was arrested in Seattle in early November 2019.
The other two suspects are in Saudi Arabia and out of U.S. law enforcement reach for now.
Lessons learned from Twitter insider threat case
Like almost every company hit by an insider threat case, some security loopholes may have been missed (or ignored) and there are lessons to be learned.
We saw this in the recent case of the AT&T Wireless Insider Threats Who Were Bribed, which happened near Seattle.
Now, in this case, the FBI included two small paragraphs within the indictment that will be of interest to our cybersecurity readers:
"A Twitter Security Engineer informed the FBI that, although Alzabarah may have had grandfathered access to view user information through an internal Twitter tool... Alzabarah had no legitimate business purpose as a Site Reliability Engineer to access user accounts."
In other words, Twitter faced some Identity and Access Management (IAM) challenges because an employee had access to information he did not need.
It appears this may have changed, and the indictment seems to indicate Twitter has shifted to a least privilege model:
"Twitter has enhanced its controls and permissions to restrict access to user information only to those whose duties require access."
By listening to the security professionals who collaborate at our SecureWorld conferences, we've detected definite momentum for this approach to IAM.
And a recent panel on this topic uncovered four questions security teams should be asking about the technology that enables their IAM programs:
- Are you choosing technology that enables you to easily manage privilege for user passwords?
- Does the technology provide easy to use and understand reports on user activities?
- Will the technology let you establish a fine-grained segregation of duties across the business?
- Does your choice work with both SaaS and on-premise applications?
Also, there is one more thing about the Twitter insider threat case that mirrors what is happening at other organizations.
Dr. Larry Ponemon of the Ponemon Institute told us about this recently at SecureWorld Detroit:
"We now know that the assets that we should be worried about are the intellectual properties of the company. Small amounts of high value information can sometimes be more important than some huge data files."
In this case, those small amounts of information were of very high value to Saudi Arabia.
Read it yourself: Twitter Insider Threat Indictment




