United States manufacturing giant Parker Hannifin recently announced the company fell victim to a ransomware attack, resulting in a data breach of employee information.
A statement from the Ohio-based corporation says the incident occurred on March 12th and it has begun the process of notifying employees whose personal information was potentially compromised.
The attack came from the infamous Conti ransomware gang, which has reemerged in the last couple months, notably forcing Costa Rica into a State of Emergency after a ransomware attack crippled the government's ability to operate normally.
Parker has an annual revenue of more than $14 billion and employs over 57,000 individuals, so it is safe to say the company is taking this incident very seriously.
Parker notifies employees of data breach
Parker's statement says that upon learning of the incident, the company initiated incident response protocols, which included shutting down certain systems. The following investigation, with the assistance of a forensic investigation firm and other third-party cybersecurity professionals, revealed that threat actors gained access to IT systems between March 11 and March 14.
The investigation also determined the unauthorized third party may have acquired certain files within Parker's IT systems. The company's statement says:
"As part of the investigation, Parker reviewed these files and determined that they may have included information related to current and former employees, their dependents, and members of Parker's Group Health Plans (including health plans sponsored by an entity acquired by Parker).
This information may have included individuals' names in combination with one or more of the following: Social Security numbers, dates of birth, addresses, driver's license numbers, U.S. passport numbers, financial account information (bank account and routing numbers), online account usernames / passwords, enrollment information, including health insurance plan member ID numbers, and dates of coverage.
For a very small number of these individuals, the files also included dates of coverage, dates of service, provider names, claims information, and medical and clinical treatment information."
Parker also said it would be offering a complimentary two-year membership of Experian's IdentityWorks to affected employees, which would help individuals detect misuse of stolen information and provides identity protection support.
Conti responsible for Parker attack
While the company did not say who was responsible for the attack in its statement, Conti did claim responsibility by posting 3% of the stolen data on its extortion site on April 1st. After a couple weeks of what one can assume to be stalled ransom negotiations, Conti posted the rest of data, 419 GB in total.
Bleeping Computer shared this image from Conti's leak site:
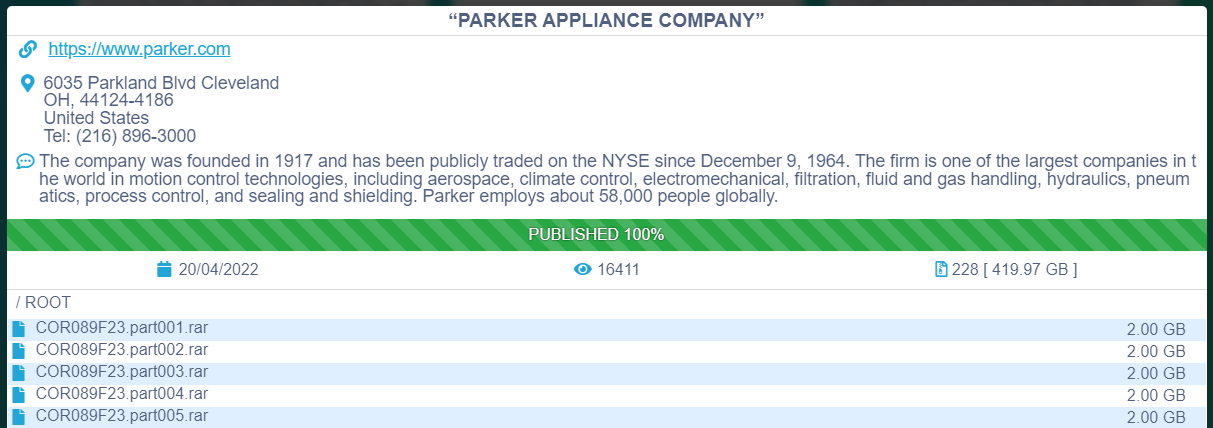
As the note says, Parker is a global leader in motion and control technologies. The company manufactures products used by companies like Boeing, AirBus, Lockheed Martin, Rolls Royce, and many more, making its sensitive data a high-value target for cybercriminals.
It is unknown if Conti threat actors were able to gain access to technical information, or if the incident is limited to employee data; though, this wouldn't be the first time Conti stole highly valuable and technical information.
In the incident involving Costa Rica, one specific threat actor claimed responsibility for the attack, who is known as unc1756. Unc1756 said the incident would be the first of many, and promised to "carry out attacks of a more serious form with a larger team." This incident took place on April 12, one month after the Parker incident, so it is unclear if the same threat actor was responsible for both.





