Quantum ransomware, a strain discovered back in August 2021, has been found to have one of the fastest Time-to-Ransom (TTR) ever in a recently observed ransomware case.
Security researchers with The DFIR Report say that it only took three hours and 44 minutes to go from initial access to domain-wide ransomware, a very small amount of time for network defenders to detect and respond, especially considering attacks often occur outside office hours and on the weekends.
They also say IceID malware was utilized for initial access by a variety of ransomware groups, including REvil, Conti, and XingLocker.
About two hours after the initial infection, the threat actors began hands-on-keyboard activity. They note that Cobalt Strike and RDP were used to move across the network before using WMI and PsExec to deploy the Quantum ransomware.
How does Quantum ransomware work?
As mentioned above, the threat actor(s) in this case was able to enter the network when a user endpoint was compromised by an IceID payload contained within an ISO image. The DFIR Report attributes with high confidence this payload was delivered through email, though they were unable to identify the delivery email.
Researchers discuss what happens next:
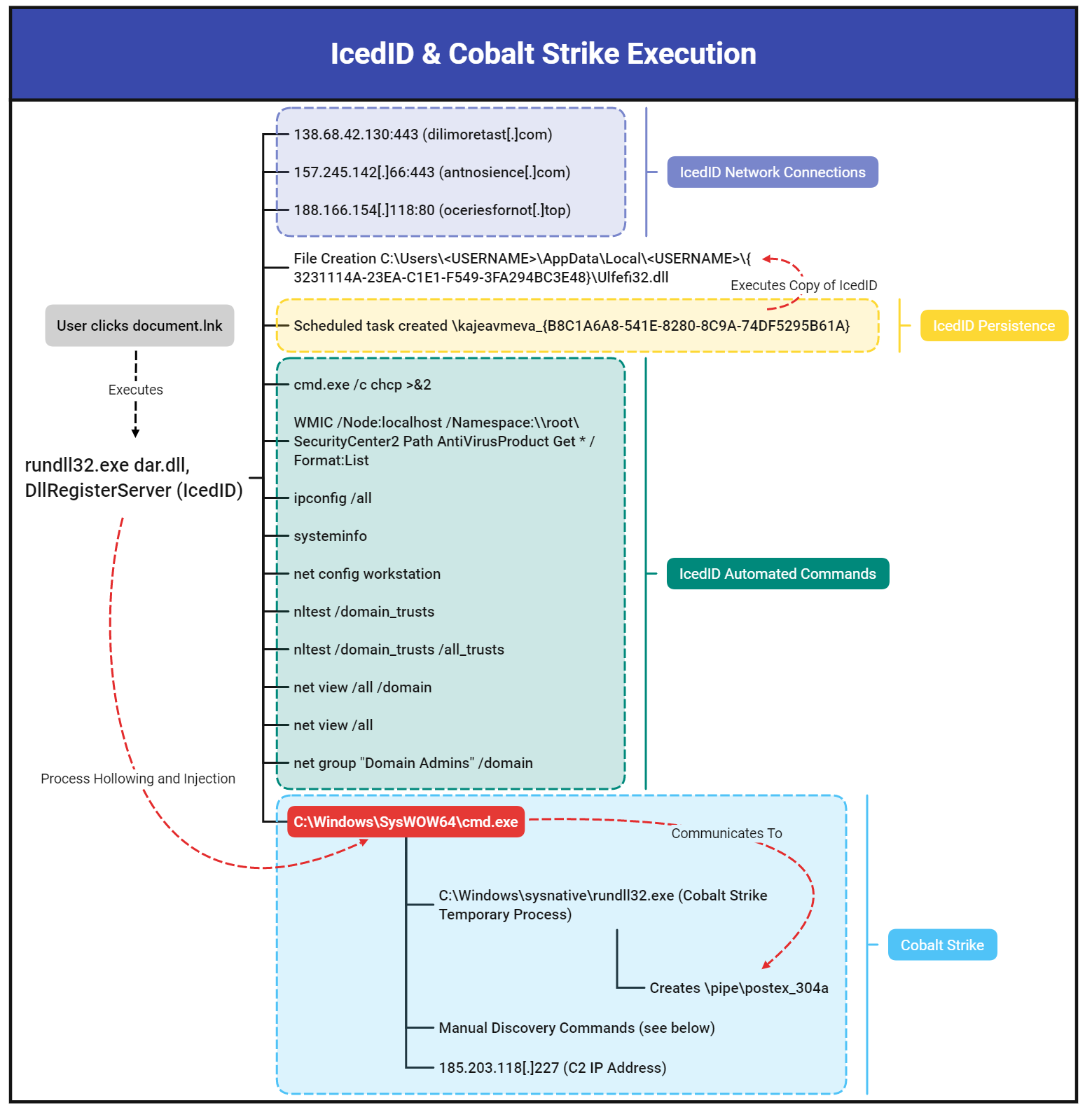
"The ISO contained a DLL file (IcedID malware) and a LNK shortcut to execute it. The end user after clicking into the ISO file, could see just a single file named 'document', which is a LNK shortcut to a hidden DLL packaged in the ISO. When the user clicks on the LNK file, the IcedID DLL is executed.
Upon this execution of the IcedID DLL, a battery of discovery tasks were executed using built-in Windows utilities like ipconfig, systeminfo, nltest, net, and chcp. The IcedID malware also created a scheduled task as a means of persistence on the beachhead host."
After about two hours, Cobalt Strike is deployed, marking the beginning of the hands-on-keyboard activity.
"This activity included using AdFind through a batch script called adfind.bat to perform discovery of the target organizations active directory structure. The threat actors gathered host based network information by running a batch script named ns.bat, which ran nslookup for each host in the environment."
The DFIR Report continues to describe the intruder activity:
"The Cobalt Strike process then proceeded to access LSASS memory to extract credentials, which a few minutes later were tested to run remote WMI discovery tasks on a server. After confirming their credentials worked with the WMI actions, the threat actor proceeded to RDP into that server, and attempted to drop and execute a Cobalt Strike DLL beacon on that server. This appeared to fail so the threat actor then opened cmd and proceeded to execute a PowerShell Cobalt Strike Beacon. This Beacon was successful in connecting to the same command and control server observed on the beachhead host.
For the next hour, the threat actor proceeded to make RDP connections to other servers in the environment. Once the threat actor had a handle on the layout of the domain, they prepared to deploy the ransomware by copying the ransomware (named ttsel.exe) to each host through the C$ share folder. They used two methods of remote execution to detonate the ransomware binary, WMI and PsExec. This ransomware deployment concluded less than four hours from the initial IcedID execution."
The graphic below shows the execution of IceID and Cobalt Strike:
Though the ransom note indicated that data was stolen, The DFIR Report says it did not observe any "overt exfiltration of data." However, it is certainly possible the threat actors used IcedID or Cobalt Strike to transmit sensitive data.
With a TTR of less than four hours, Quantum ransomware is something that network defenders might want to read up on and learn the best ways to defend their organization.
For more technical information on the speedy ransomware strain, read The DFIR Report on Quantum ransomware.





