The 2019 State of the Phish Report is the most robust State of the Phish we’ve ever seen
Does that approach work? More on that later on.
It was extremely helpful to listen to the findings in the 2019 State of the Phish web conference, which is available on demand. The context the authors provide and the audience Q&A session helped surface additional details and related strategies.
2019 State of the Phish Report, data usedThe 2019 State of the Phish Report is recognized as a state of phishing attacks benchmark report for a reason. It is built on big data, including:
- Results from tens of millions of simulated phishing emails sent by Proofpoint customers
- Nearly 15,000 survey responses from InfoSec professionals on multiple continents
- Insights from an additional 7,000 technology end-users
- Data comes from across verticals: 16 industries in all
3 major findings in the 2019 State of the Phish Report
For the sake of brevity, we’ve picked three significant findings, of many, from the 2019 report.
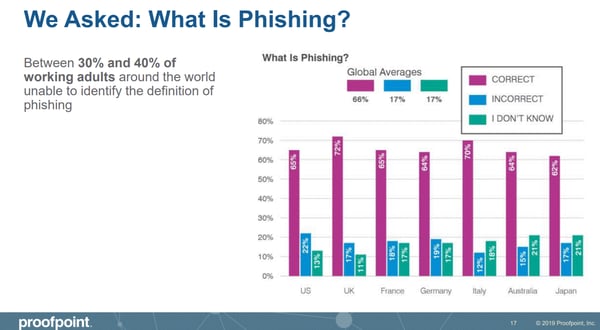
1. Too many employees still cannot answer the question, “What is phishing?”The bar chart (below) shows responses to this question from employees in seven countries around the world. In the United States, 35% of survey respondents still cannot define phishing from a multiple choice list of possibilities.
Gretel Egan, Security Awareness and Training Strategist with Proofpoint, framed the seriousness of this statistic.
“I really like to think about in terms of organizational numbers. Like 100, 1,000, or 10,000 in your organization. What does it mean if 40, 400, or 4,000 of your employees don’t know, at a fundamental level, what phishing even is?”
She says one factor is that end users may not understand the language InfoSec is speaking.
“If not, there’s a good chance you’ve lost a big percentage of your users before you even begin to address the risk from phishing attacks.”
And she says it is evidence that security awareness is still in its infancy when it comes to adoption and implementation.
2. Digital natives in your organization are not security nativesThe 2019 State of the Phish Report also uncovered evidence about Millenials and younger employees. Being a digital native does not mean you “get” cybersecurity. And here’s something else (below) worth noting: baby boomers performed the best in this category!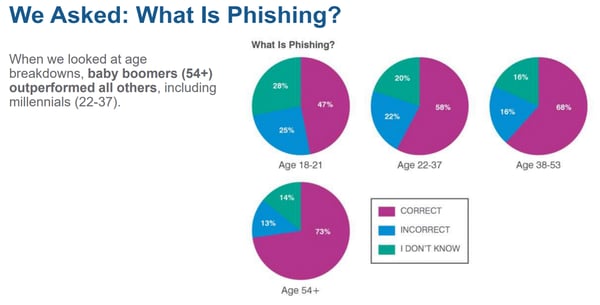
The Proofpoint team says one thing they see boosting security awareness across employee demographics is making sure they understand that cybersecurity can benefit them personally in their lives. You’re asking them to learn something new that benefits both the organization and the individual.
3. Carrot vs. Stick: consequences for repeated failureDuring the State of the Phish web conference, there was considerable discussion about an organization’s culture and the impact culture has on security awareness programs. This includes what to do about employees who repeatedly fail when it comes to phishing—whether simulated tests or real attempts.
Here was the biggest surprise in this area, shared by former Alcoa CISO Alan Levine, who is now a Cybersecurity Advisor for Proofpoint Security Awareness Training.
“We asked, do you use a consequences model and punish those who repeatedly click on simulated phishing emails when they should not? And if you do, is it working? The surprising thing about most consequence programs is that most are unsure if that approach even works.”
Check out the numbers (below):
Levine says many organizations are unsure how to collect the data on this and asked if you should be doing something you are not able to measure.
In his experience, employees respond more significantly to the carrot than the stick.
“Reach out, communicate, with help,
He also covered what to do if you are a security awareness leader that has inherited a consequences model and how you could begin to change the culture if you would like. And also, what to do if your culture does not support simulated phishing tests at all.
How to watch State of the Phish 2019 webinar, download PDF
Here are two resources relating to the new State of the Phish report.
Listen/watch and earn CPE credits: 2019 State of the Phish Web Conference [on demand, includes report PDF]
Report download: 2019 State of the Phish PDF
The full PDF includes about 90% more than we’ve covered here. The insights will help you make informed decisions on your Security Awareness program or get you started toward a