We just finished reading an AWS white paper on building threat hunting capabilities in a cloud environment, and it paints a clear picture of where your security maturity should be as you begin this process.
"The infrastructure is built, a patching plan is in place, firewalls are locked down and monitored, assets are managed, and the SOC team is responding to alerts from the security sensors. When basic security hygiene is implemented, the threat hunting team needs to start evaluating infrastructure for any threats and undetected breaches."
Each infrastructure features moving parts, multiple operating systems, networking tools, and custom applications. Security teams need to know which threats to look for, how to prioritize them, and where to start hunting.
And then you add the nuances of doing this in a cloud environment.
Approaching threat hunting in the cloud
So how should you approach threat hunting in the cloud? For starters, create a premise or hypothesis:
"Threat hunting starts with the premise of, 'Our main web application is facing the internet and may be the victim of a web attack. Let's see how we can determine that.' Or maybe a weak indicator sparks suspicion: 'Multiple failed SQL injection attacks in a row. The web server performance is slower. Let's look for potential intrusions.' There are multiple scenarios in between that can all be considered threat hunting."
Next, create your threat hunting loop:
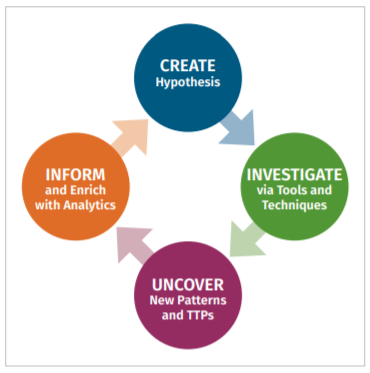
- Create a hypothesis
This could take you in a lot of different directions, so determine the organization's most valuable and/or at-risk areas to set priorities. - Investigate with tools and techniques
"To do this, data must be collected, understood, analyzed and viewed comprehensively. Threat hunters must also pivot through different types of logs and explore unstructured or partially structured data. In AWS, several tools help with this process."
Teams can easily pull logs from any system and into Amazon CloudWatch. That pathway looks like this: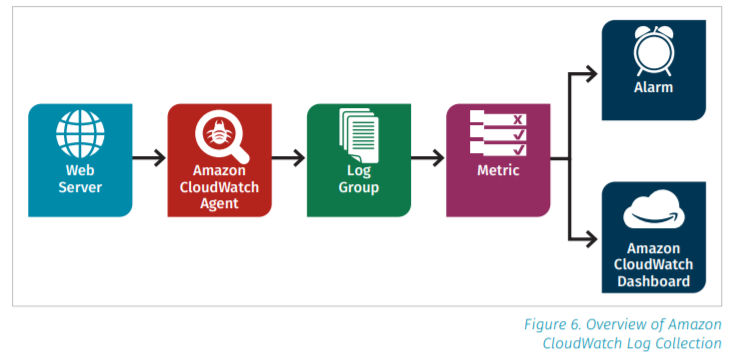
AWS CloudTrail is a cloud native service that gathers and allows an analysis of Amazon Web Services API requests.
3. Uncover patterns and TTPs
"The team should become part of the threat modeling processes, helping
the architecture and operations teams identify the cloud infrastructure that needs to be secured and evaluated. Changes such as improved monitoring, reduced chaotic deployments and better segmentation of infrastructure can all make threat hunting easier without losing operational capabilities."
4. Inform and enrich with analytics
The threat hunting team has to strike the right balance of how much data to capture. AWS makes it easy to collect VPC logs showing data connections in and out of the VPC, API calls with AWS CloudTrail, and Amazon S3 access logs, among others. Then, using the attacker techniques, the team will focus on identifying the gaps in information and how to retrieve it.
The white paper then goes through a series of use cases around post-exploit detection in the cloud, enriching the data for analysis, and creating a cloud-based SIEM and SOAR environment.
"Threat hunting is all about proactive analysis of data to detect the anomalous behavior that is undetectable by the security products. As the threat hunting team's analytics become more sophisticated, it may begin developing a set of repeatable analytics, enrichments or data gathering steps. If it's repeatable and articulate, it can be automated."
Use case: threat hunting in the cloud
Here's a look at one of the use cases for threat hunting in the AWS cloud.
"In a cloud environment of automation, once attackers gain access to the web application VM, they will want to use the MITRE ATT&CK tactic called Discover to find other services of interest, such as an accessible Amazon S3 bucket with the command ListBuckets."
In AWS, the case study looks at the web application which has access to Amazon S3 buckets for configuration.
"The IAM role does not allow listing of buckets. Automated systems likely already know the resources they need to interact with, so listing potential names is unnecessary. From the Amazon EC2 instance, listing buckets results in an error, as shown in Figure 7."
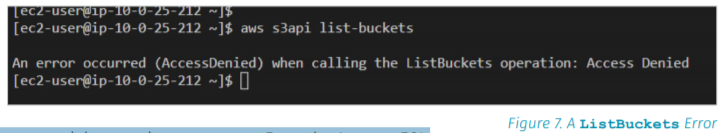
This is where AWS CloudTrail comes in.
"It gathers and allows an analysis of Amazon Web Services (AWS) API requests. AWS CloudTrail, using the Amazon EC2 ID as the username, looks at the ListBuckets as an indicator. There is an AccessDenied error code, as shown in Figure 8."
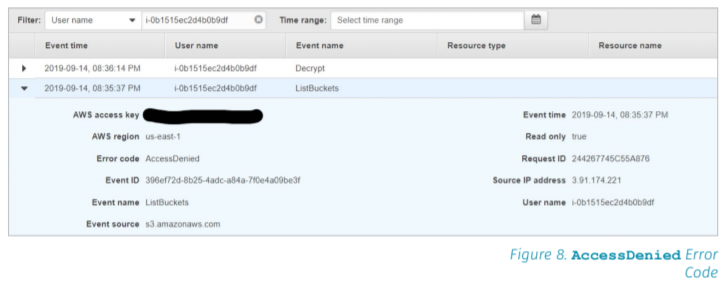
Each event like this has a unique event ID and data table which a threat hunting team can then filter, carve, and format.
For more use cases and strategies:
- White paper: Enabling a Threat Hunting Capability in AWS
- Webinar: How to Build a Threat Hunting Program in AWS Cloud
Threat detection in the cloud
Also, if you've delayed moving to the cloud because you were afraid of losing visibility and the ability to detect threats, you may be surprised to hear how dramatically things have changed.
Amazon Web Services puts it like this:
"One major concern security teams have is losing visibility and detection capabilities when their organization moves to a cloud. While this might have been true in the early days of cloud services, these days providers are announcing new threat detection features and offerings almost every month. These new services open up the possibility of adjusting traditional network- and host-based monitoring to support intrusion detection in the cloud."
In a related white paper, AWS and SANS walk you through the steps for cloud visibility and threat detection, including:
- Data collection
- Intrusion Detection and Prevention Systems (IDS/IPS)
- Event management and analysis
And then putting it all together to push into automation.
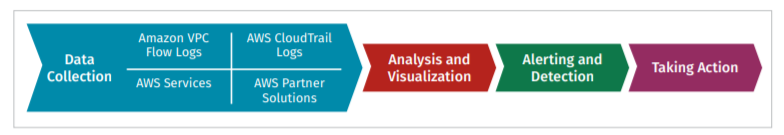
"A security team that takes into consideration the recommendations of the previous sections and makes the time investment to fit together the different detection components is able to use cloud-native services and define automated detection and remediation workflows. By reducing the amount of manual labor in the team, the team has more time to focus on other areas of information security."
AWS announces Amazon Detective to simplify threat detection
And the tools for threat detection in the cloud keep getting more robust and simpler to use.
AWS recently announced a new tool called Amazon Detective; here's what it can do:
"Amazon Detective simplifies this process by enabling your security teams to easily investigate and quickly get to the root cause of a finding. Amazon Detective can analyze trillions of events from multiple data sources such as Virtual Private Cloud (VPC) Flow Logs, AWS CloudTrail, and Amazon GuardDuty, and automatically creates a unified, interactive view of your resources, users, and the interactions between them over time. With this unified view, you can visualize all the details and context in one place to identify the underlying reasons for the findings, drill down into relevant historical activities, and quickly determine the root cause."
And that is a significant reason to move to the cloud, isn't it?
Take advantage of cloud native tools to increase automation and maintain visibility while limiting the time investment from your team.
RESOURCES:




